[Writeup] Ananas
Description
In an unfortunate turn of events, trupples tried to become a camboy, It didn't turn out so well... Here is what the family firewall recorded...Ananas was a reverse challenge in HackTM ctf 2020 Qualifications, I love packet analysis challenges, and this one was basically reverse in a pcap file, its my lucky day.
Note: I solved this challenge with the awesome @d35ha.
I downloaded the challenge, opened it with wireshark:
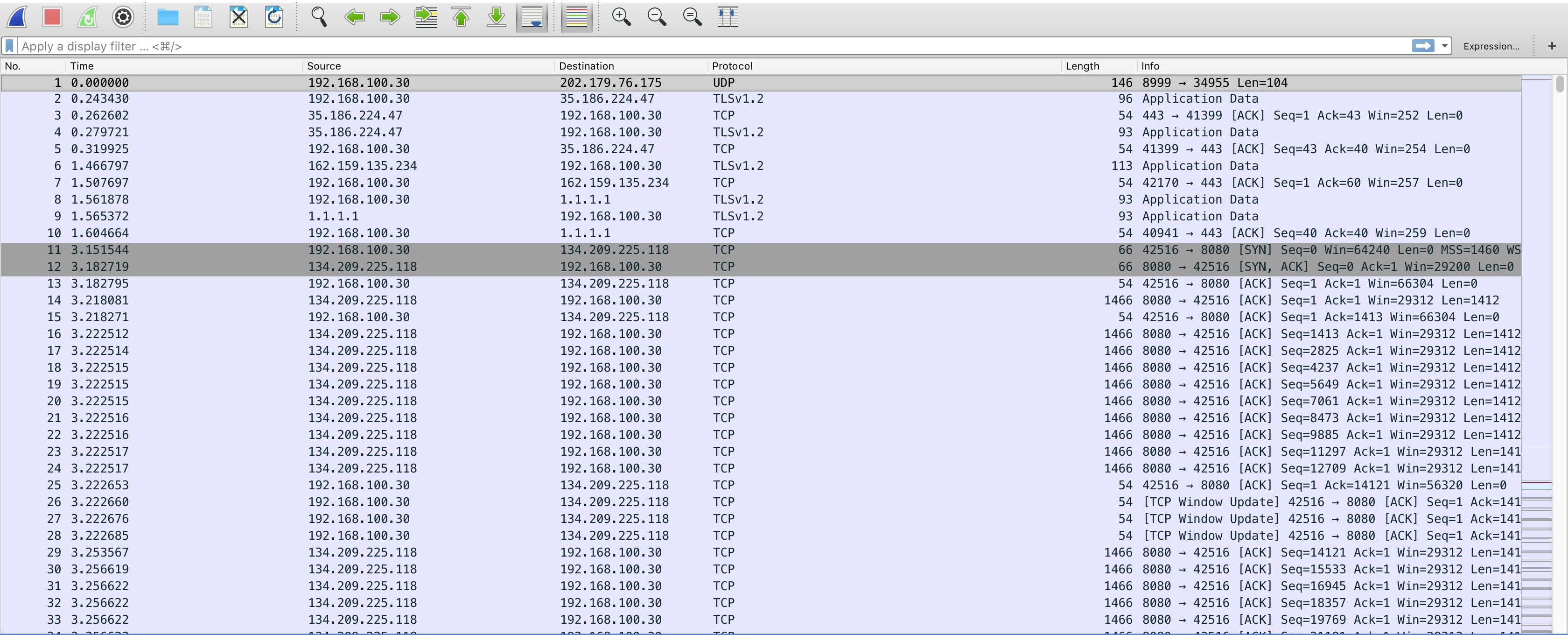
Going through the values, I noticed some pattern, there was a connection going between 134.209.225.118 and 192.168.100.30, I added a fillter to just check those ips:
(((ip.dst == 192.168.100.30) && (ip.src == 134.209.225.118) )|| ((ip.dst == 192.168.100.30) && (ip.src == 134.209.225.118) ))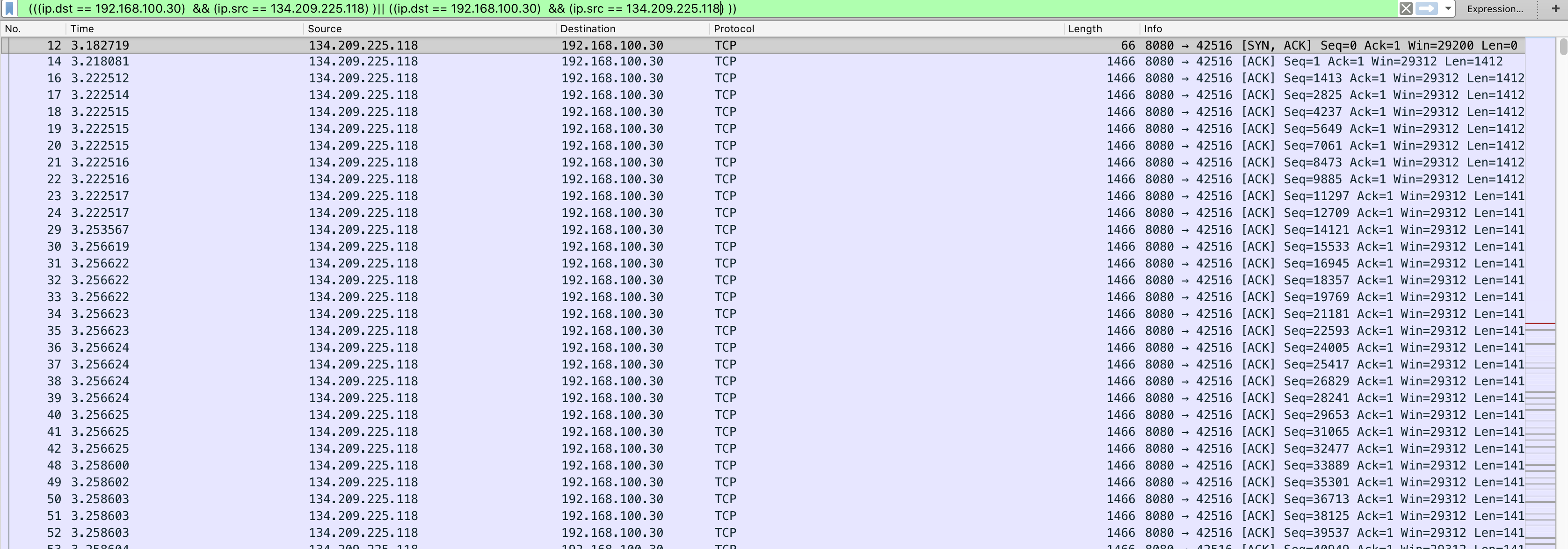
It looked like some data was getting sent from .118 to .30, checking the packet data:
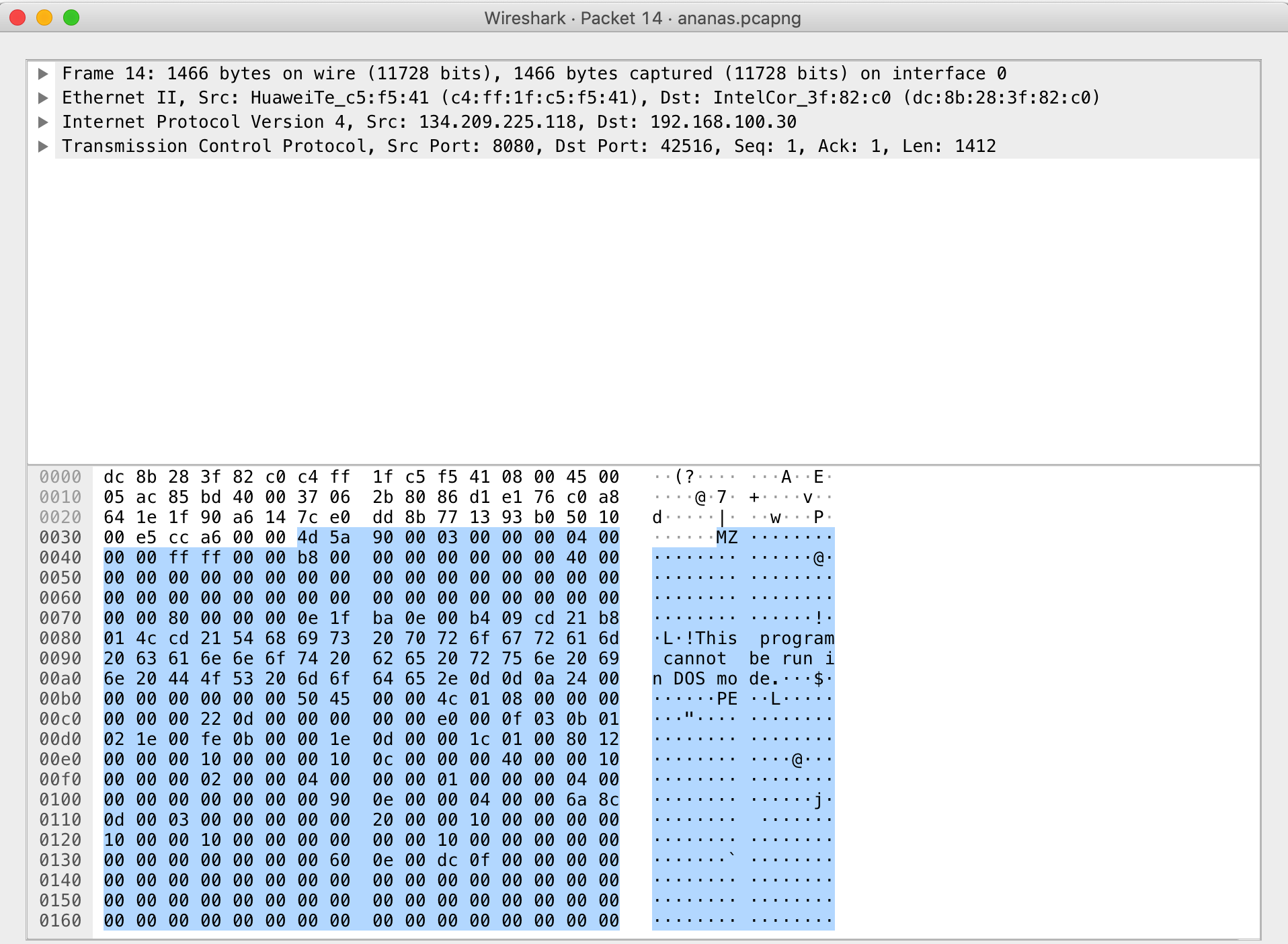
Awesome so we found a pe file, so .118 was sending an executable to .30, trupples(who my guess is .30) tried to become a camboy and firewall recorded.
hmm...you get what that is? lets analyze the file.
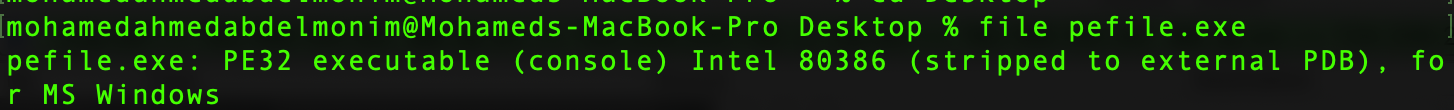
Opening the file in IDA:
The binary was stripped and it used some imports so there were a lot of functions, but the main wasn't that big:
Going through the binary I found Winsock getting initialized, so I assumed that it must be the binary sending the packets.
One of the big functions in the binary had error strings:

and according to the ctf golden rule, Google is your friend, I just copied the string to google and I found
that:
Great so the reverse process is now a lot easier, we know what each function does since we have the source code!
Changing some symbols on ida and we get this:
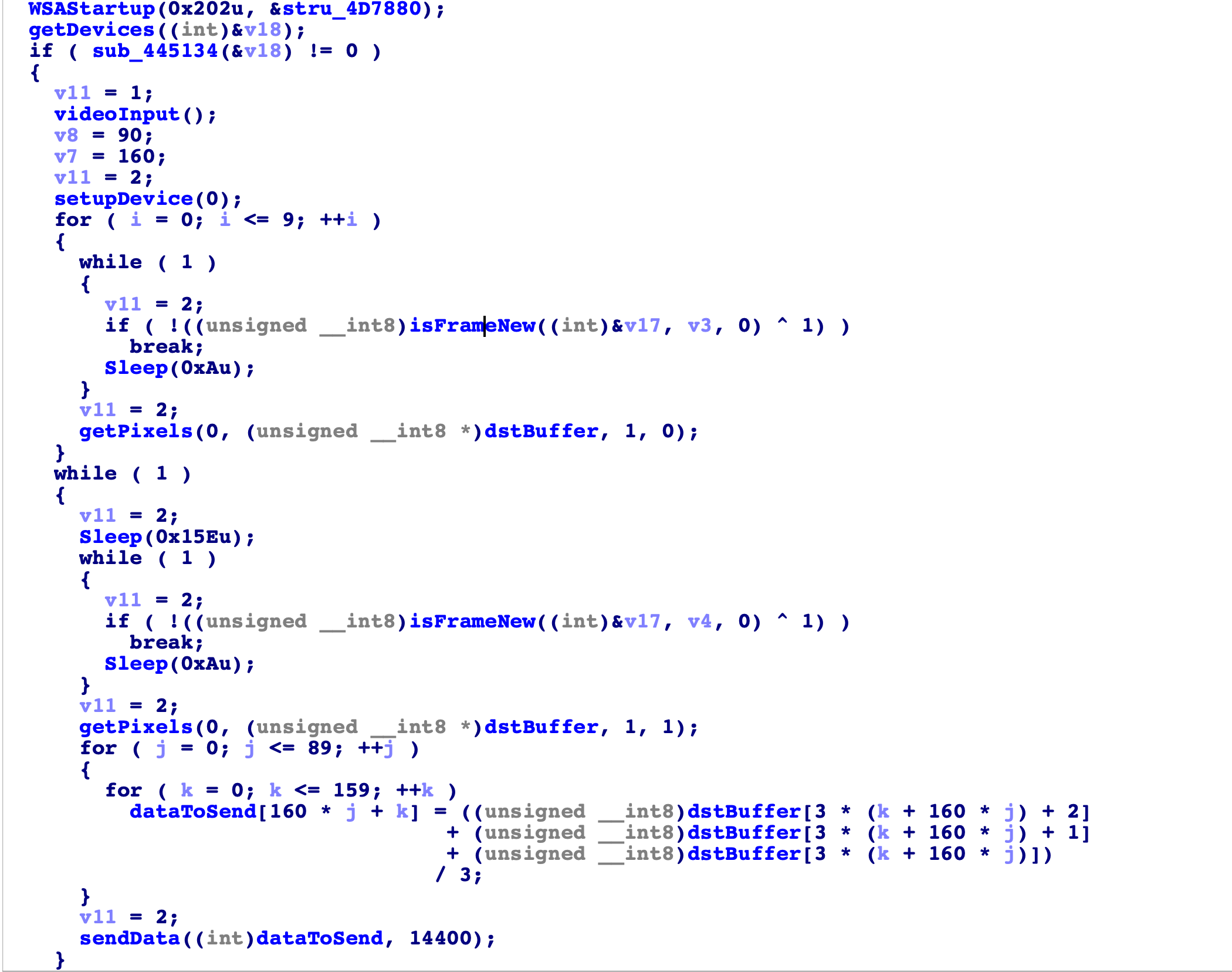
So turns out its a malware that opens the camera,records videos and sends them a frame by frame to the server, which is .118 .
The function that sends the data alters them in a way, we had to analyze it:
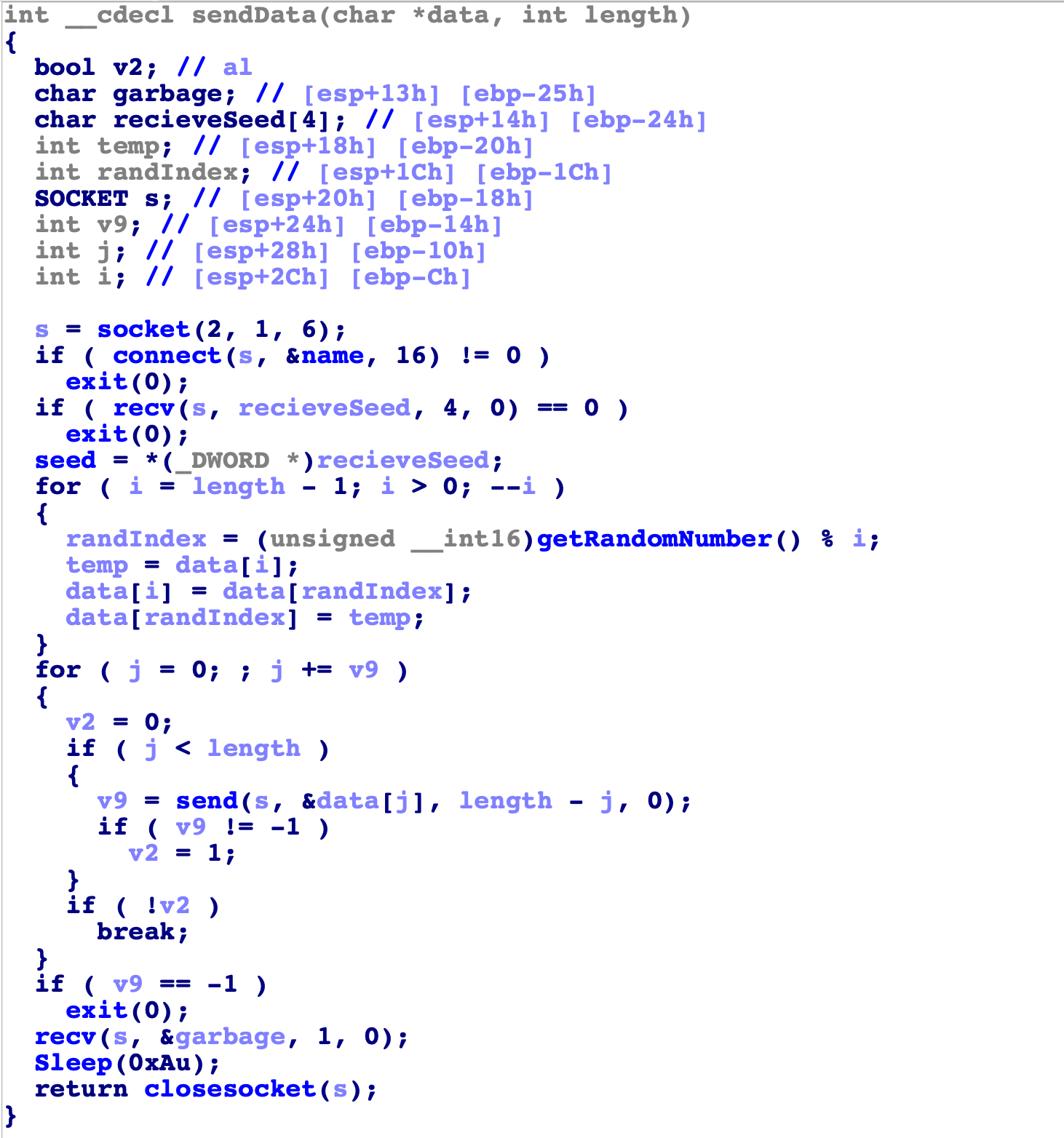
So the steps are:
- .30 recieves 4 bytes from .118 and uses them as seed
- Generate N random numbers where N is the length
- For every generated index it will swap 2 bytes.
- It sends the frame whose size is 90 * 160 = 5400
- .118 replies with a byte to confirm recievinig
So now we know what we have to do:
- Reverse the swapping algorithm (since we have both the seed and the randomization algorithm it won't be hard).
- Parse the packets to extract the seed and the sent data.
- Apply the algorithm to to the data in order to retrieve the actual bytes and use them to make an image, the flag is probably in the video.
Extracting the packets:
We need a good filter to use:
(data) && (((ip.dst == 192.168.100.30) && (ip.src == 134.209.225.118) )|| ((ip.src == 192.168.100.30) && (ip.dst == 134.209.225.118) ))(data): To make sure the packet has data.
(((ip.dst == 192.168.100.30) && (ip.src == 134.209.225.118) )|| ((ip.src == 192.168.100.30) && (ip.dst == 134.209.225.118) )): To get the communication.
Extracting the data using tshark:
tshark -r ananas.pcap -q -Tfields -e data -Y "(data) && (((ip.dst == 192.168.100.30) && (ip.src == 134.209.225.118) )|| ((ip.src == 192.168.100.30) && (ip.dst == 134.209.225.118) ))" > data.txtParsing the extracted data:
recieved=open('data.txt','r').read().split('\n')[1:-1]
for i in range(0,len(recieved),4):
seed=recieved[i].decode('hex')
seed=struct.unpack("The reverse function:
def reverse(data):
tempIndex=[i for i in range(len(data))]
tempData=[0 for i in range(len(data))]
tempIndex=realReverse(tempIndex)
for i in range(len(tempIndex)):
tempData[tempIndex[i]]=data[i]
return tempDataI spent a lot of time checking what was wrong in my script, and it was in the way C handled data types and how python does:
def GetRnd():
global seed
seed = ((48192 * seed) + 4717718)&4294967295
seed ^= (seed >> 7)&4294967295
seed ^= (seed << 17)&4294967295
seed ^= (77 * seed)&4294967295
return (seed / 0x4D2)%0x10000Running the script and we get the pictures, I combined them to a gif:

HackTM{f2c05fb92c647c19aaf31ca67369d7b3b399c5b4c348edc23d03a97992203e3f}To the next writeup!

